Cyber security still underestimated
It seems that cyber security is talked about all the time in the business world, but the data remains inexorable – it’s still not enough. Online fraud is taking on more and more new forms, and according to the report State of Enterprise Cyber Risk in the Age of AI 2024 as many as 10% of enterprises in the United States have never conducted a security audit. Slightly more than half admit that they look for security vulnerabilities no more than once a week. What’s more, as many as 65% of those surveyed still rely on security plans that have been prepared for two years or even longer.
Given how quickly new cyber threats are emerging and how those that are known in theory are evolving, there is a huge scale of oversight. However, the authors of the report in question point to the great potential for the development of artificial intelligence in the context of enhancing cyber security in the business sector. However, it should not be forgotten that cyber criminals also have access to AI-based tools.
We don’t have reliable data on companies in Poland, so it will be safe to assume that it is similar or slightly worse. At the end of the day, however, the most important thing is to answer the question yourself: is my company putting a strong enough emphasis on security issues? Here’s what companies face – even if they don’t know it.
What is phishing?
Phishing is – colloquially speaking – catching victims for bait. The association with fishing is not coincidental. In English, fishing is fishing, which sounds the same as phishing precisely.
In phishing, an online scammer sends messages that are disguised to pretend to be from a reliable source. In this way, it tries to obtain sensitive data from its target, such as:
- logins and passwords,
- payment card numbers,
- bank account numbers,
- Access to accounts (private and corporate),
- address details.
This, of course, is not the end of the list – fraudsters obtain all kinds of data this way – the ones they just happen to need. How does this happen?
Bait above all
The means of executing a phishing scam are usually emails, SMS, instant messaging or phone calls. In the case of SMS, we may also encounter the term smishing, and scams carried out via phone calls are often called vishing.
An effective lure is one that inspires confidence. This will often be an email that looks exactly like one we get from a trusted sender, a message written in the style of someone we know, a text message that looks like marketing, or a conversation with a confident person claiming to be – for example – an employee of a trusted institution.
How to verify the sender? In the case of email phishing, the matter is relatively simple – you need to verify the sender’s address, as this is what often helps unmask the scammer. It’s not enough to glance at the sender’s field – the content there is easily crafted to display anything – even the name of the U.S. president.
Here’s an example: in the main mail view, the sender displayed only as Mail. The subject line not only contained the recipient’s name, but also informed about the shipment. Who among us hasn’t ordered a package online recently? This very fact is being exploited by cybercriminals, trying to get users to click on the link left in the message:
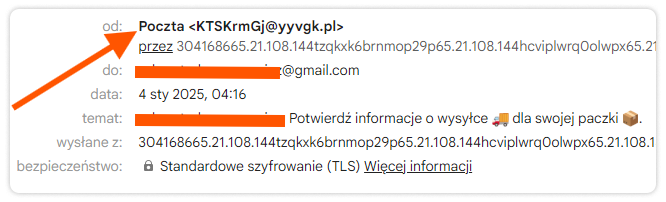
In the above example, even a quick glance at the email address lets you know that we are dealing with an attempted scam. The whole message, moreover, is prepared carelessly. However, this does not mean that we are safe – such messages are still sent, because under certain conditions they have to work. What’s more – many scammers are much more meticulous, and distinguishing their messages from the original is sometimes much more complicated.
What is the purpose of phishing?
The most important thing in phishing is to get the victim to interact – this involves clicking on a link provided in a message, downloading a designated application (such as one that infects a phone) or sharing data during a phone call. After going to the address indicated by the fraudulent link, for example, the user may end up at a phishing site – one that looks twinned with the login page of the bank where the scammer’s victim has an account. The next step is simply to log in, giving the scammer access to the account.
The obvious and ultimate goal of phishing, then, is to gain access to bank accounts or obtain sensitive data to sell. These individuals often only need to get the details of an email account, which will allow them to hack into and change the passwords of most other accounts a user may have.
Important!
The most dangerous variety of phishing is so-called spear phishing, which gets its name from whale hunting. Spear means spear in English. Spear phishing is nothing more than an attempt to attack a specific person or organization, that is, a scam targeted and planned to harm a specific target. It’s particularly dangerous because spear phishing scammers usually have much more knowledge about their chosen victim than those who attack en masse.
There is also a method of phishing called whaling, or simply whaling. The idea is to attack in a precise way a decision-maker or a person holding a high position in the company. All this in order to – after a successful attack – get access to sensitive, secret and valuable data about the company, customers or competitors.
How to defend against phishing emails?
Here are some basic tips to help you and your company’s employees protect themselves from data loss due to phishing. Each of them can (and even should!) be applied right away, without any preparation.
Always check what you click on
You can check links in emails or on websites by hovering over them with your mouse cursor. Most web browsers will then display a bar with the destination address at the bottom of the displayed page. On mobile devices, simply hold down the hyperlink longer to display the address hidden underneath.
Look at the addresses you visit
They can be confusingly similar to the right ones – sometimes one letter or dot put in the wrong place will get you to a completely different site than you expect.
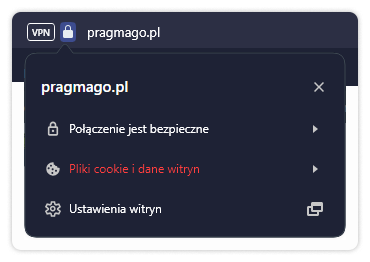
Be careful when logging in
When you log in to your mail, bank account or other important sites, check the address bar in your browser. Any site where you leave your data should be protected by an SSL certificate – you’ll know this by the padlock icon to the left of the address. When you click it, you will get detailed information about the certificate:
Regularly update the browser you are using
If possible, enable automatic updates. Outdated browser versions are more vulnerable and will not help you detect fraud attempts.
Report suspicious messages
If you receive a message with a link that may be a scam attempt, don’t leave it without reacting. Report the message to your network administrator, do not open the e-mail, and under no circumstances click on the link.
How to protect your business from phishing?
Your company should know how to defend against phishing. Simply sending out a message with best practices (such as those listed above) to all employees may not be enough. It’s worthwhile to put specific measures in place within your organization to protect employees (and company data) from fraud in the long term.
Better security features
A password manager, two-factor authentication, up-to-date antivirus and anti-malware software, strongly secured Wi-Fi networks – all solutions that by themselves won’t make phishing stop affecting your business, but will clearly help detect and repel attacks.
Phishing training courses
Your employees need to know what to look out for when working online. Provide them with training on phishing protection and make sure that participants have the opportunity to test their attentiveness. The training doesn’t have to end with an exam, but you can ask the trainers to prepare a quiz to make your employees aware of how alert they are to fraud attempts.
Secure internal communications
Fraudsters most often attack by email for one simple reason: it’s the easiest. So your company’s internal communication doesn’t have to be by email. While this is by far the most convenient solution (especially when communication is internal only in part and sometimes intertwined with external communication), consider using a communicator that will only serve internally and formulate clear rules for its use.
Spoofing – what is it?
Another threat lurking for companies and consumers on the Internet is spoofing. This is a type of fraud in which an attacker impersonates an employee of an institution or a specific individual in order to defraud.
We are familiar with high-profile cases in which a defrauded person sends large sums of money to scammers thinking they are financing the cost of an urgent surgery for Brad Pitt or the cost of flying Scarlett Johansson into the country. While articles on this subject tend to evoke general hilarity, in reality these are just glaring examples of a real danger that can affect everyone.
Spoofing in a nutshell
In this technique, a scammer impersonates an email address, phone number or IP address and contacts the victim. This is a more sophisticated form of phishing that resists basic defense techniques. It won’t do anything to check the phone number of the caller, because – if the scammer has prepared well – it will be a valid number, the same one found on the website of the bank or other institution impersonated.
So if anything raises your doubts, follow a few steps to help protect yourself from fraud.
Be careful
This is a general rule, but it’s worth keeping it in the back of your mind at all times, especially when you are contacted by someone claiming to be an employee of a bank or other important institution. If you’re not sure if you’re talking to a real consultant, write down the number he or she is calling from, compare it with the bank’s official number and call back if it’s correct.
Remember that scammers only impersonate the institution’s number, they do not actually have access to it. So if you call the right number, you will be connected to the bank, not the scammer.
Once connected to the institution, ask if anyone has contacted you and provide the personal information of the person who called you – if they introduced themselves.
Find out how to verify the employees of the institution
Many banks and financial institutions provide detailed information on how to verify that a caller is actually an employee of the institution. Visit your bank’s website and check so that you can easily verify who contacted you in the future. Some banks provide the ability to verify in a mobile app.
Don’t give out data, don’t click on links
No employee of a bank or other institution will ask for private data, passwords, access codes or other sensitive information. If such a request is made by a caller, end the call and report the matter to your bank.
Behave similarly if a scammer sends any links or attachments. Do not click on or open them unless you are sure what they contain and who the sender is.
Pharming – what is it?
When describing phishing, we mentioned phishing sites. These are websites that – not infrequently successfully – pretend to be the official website of a bank, store or other portal to get victims to log in and thus leave their access data.
Creating these sites and “swapping” the right ones for fraudulent ones is precisely one type of pharming. In pharming, scammers install malware on their target’s computer that redirects the user – unnoticed – to a site appropriately prepared by the scammer.
Example:
Mr. Rafal wants to make some money transfers. He starts his computer, not knowing that it is infected with malware. He turns on his web browser and types in the address of the bank’s website. At that moment, a program running in the background launches a redirect and instead of the bank’s website, Mr. Rafal ends up on a site prepared by the fraudster.
The site looks identical, so – unless Mr. Rafal is far more cautious – instead of logging into the bank’s site, he will enter his account access data into the login form, and the latter will send it directly to the scammer’s database.
How do you defend yourself against pharming?
In many cases, due caution should suffice. Here are three simple ways that will greatly enhance your ability to fight pharming.
Secure your network connection
A popular and often disastrous mistake is to stay with the password to the network (home or business) given by the connection provider. It’s a good idea to give a strong password to both your Wi-Fi network and your router. A secure password should contain numbers, upper and lower case letters and special characters. You should also change your password from time to time for security.
Always check the address bar
We already mentioned this when discussing phishing. If you go to the website of a bank or other important institution, as well as places where you log into any account, verify that the site’s address matches and that it has an SSL certificate (the padlock icon to the left of the address) before entering your login and password. Also verify who the certificate provider is.
Take care of your antivirus software
Although the effectiveness of so-called “antiviruses” is sometimes debated, the matter is trivially simple: it is better to have any protection – even imperfect – than none at all. However, in order to realize the potential of malware tools, three rules must be followed:
First: regularly update your virus databases.
Second: regularly scan your computer for threats.
Third: carefully read the messages sent by the software.
It is worth paying special attention to this last rule – many threats find their way onto users’ computers despite the fact that antivirus systems have detected them. Often, computer users machinically disable notifications or allow applications from an unknown source to run in order to do what they intended to do as quickly as possible (and not waste time searching for alternatives).
Block the ability to install software on company computers
Many companies are taking this step to increase the security of company computers. This is because there have been known cases in which employees have downloaded applications from unknown sources, which over time turned out to contain malware. Blocking installations is one way to reduce the likelihood of fraud.
Spam and spamming – what is it?
We all face spam, i.e. receiving unnecessary, unwanted, often annoying and sometimes threatening messages. Although declaring war on spam seems to be as effective as fighting windmills, leaving unwanted messages alone is definitely the wrong solution.
In 2023, about 45% of all e-mails were spam. By 2024, that already high percentage had risen to 46.8%. The problem affects everyone without exception – what’s more: some Internet users complain that it is not uncommon to receive more unsolicited messages than those they actually expect.
Where does spam come from?
Our email inboxes receive dozens of unwanted messages a day. How do they get there? Email addresses circulate around the network in ways that – at this stage – simply cannot be controlled. Data leaks, purchased databases – these are all ways in which spam authors come into possession of hundreds of thousands of addresses. E-mail marketing today cannot rely on spamming, but for years it was not obvious.
Spamming is usually a mass activity – an estimated one hundred billion unwanted messages are sent worldwide every day. Your mailbox probably catches most spam, lumping it automatically into the appropriate category. However, some of the unwanted messages find their way to your inbox, so once again we urge you to be extra careful.
If an email seems suspicious, there’s no point in even opening it. Instead, report it as spam, and if you have to, block the sender so they can’t send any more messages to your email address.
Is there spam beyond email?
The answer – unfortunately – is yes. Spam has long ago reached SMS, instant messaging or social media inboxes. What’s more – spam combined with impersonation is popular, especially on social media. Scammers who gain access to a person’s social media account often use the opportunity to reach out to his or her friends in order to phish for data or to conspire to click on a link containing malware.
We’ve mentioned this before, but it’s worth emphasizing – receiving a message from a known SMS number, from a contact on LinkedIn or from the email of a company you do business with doesn’t mean that everything is fine. That’s why it’s so important to carefully read the messages you receive and pay attention to any deviations from the rule (no footer in a business email, different style of message writing, shortened links, etc.).
How to defend against spam?
Unfortunately, there is no software that will completely eliminate spam from all communication channels. However, there are a few things we can do to reduce spam and not fall victim to scams.
Author verification
If you receive a message from an unknown sender from whom you did not expect a message – you should ignore it, delete it, or preferably block the sender and report the fact that you have received spam to the network administrator (for example, at the company). If it seems to be a known person, it is worth taking – one by one – the following precautions:
- Check the sender’s e-mail address carefully for typos. If even one character doesn’t match – it’s spam.
- Read the content of the message carefully and pay attention to its design. If the content is questionable or the layout of the email is not up to standard, contact the sender and make sure the message came from him.
- If the content of the message includes links and encouragement to click – be very careful.
- Move your mouse over the hyperlink and check where it leads. If you’re still not sure, go back to step 2, that is, verify that the sender intended to send you that very link.
- If the sender has used an abbreviated link (it will be visible as, for example, bit.ly, cut.to, tiny.url and the strings following this sequence), do not click. In business correspondence, link shortening is rarely used. However, if it happens and you assume that it is the actual sender who decided to shorten the link – go back to point 2.
After going through the above steps, if you are still not sure whether the message is trustworthy or you already know that it is spam, you can:
- report the message as spam,
- remove it (preferably with prior notification),
- add the sender’s address to the blacklist,
- Suggest to the network administrator to add the sender’s address to the “gray list.”
Important!
Greylisting is a slightly more complicated technique than simply adding to a blacklist of senders. Emails sent by a greylisted address will be automatically rejected by the recipient’s server on the first attempt to join. The sender will receive a message that the email cannot be delivered to the specified address. If it is spam, the sender is unlikely to send the email again – it is more profitable to send spam to more new email addresses.
Summary
The list of threats lurking online is long and constantly changing. The best defense against fraudsters is constant vigilance and adherence to the principle of limited trust. Taking care of your company’s security, on the other hand, should not be limited to these two points. Ensure regular security training for your employees, and update security whenever possible. Check what software is installed on company computers and take care of network security.


